Concerned About Securing Your Atlassian Cloud?
Atlassian prides itself on putting security first, even ahead of feature development in its products. When security incidents do occur, they prioritize transparency and fixing the issue.
Reading about security incidents concerning products we use can understandably leave us wondering what to worry about and what not to. In this complicated security and compliance landscape, CIOs, CISOs. and security-minded personnel should know what the best practices are, and why.
In this blog post, we will provide you with five best practices for effectively managing internal security threats within your business. Additionally, we are excited to introduce Beacon, the latest security tool by Atlassian. Discover how Beacon’s advanced features, including real-time updates and dependable visibility, can bring assurance to teams as they monitor and detect security risks.
Table of Contents
Internal Security Management
It’s vital to be clear on what you can and cannot control, and to focus on what you can. You can’t control whether a third party vendor has a breach, but you can, for instance, control what access their employees have to your system, and you can monitor your systems for unusual activity. You can’t control whether an exploitable defect is discovered in an Atlassian product – but you can, for instance, ensure every employee has no more access or permissions than they need, to minimize the damage if a user account is compromised, and you can monitor your systems for unusual activity.
If you’re using Atlassian Cloud products, the good news is that you’re already benefitting from the latest security improvements. But it is extremely difficult – and arguably impossible, given the complexity of software and tech interdependence – to achieve a perfectly secure environment all the time. So let’s look at the big picture to identify what you can do.
Top 5 Best Practices
#1 Create a Culture of Security
Security doesn’t just magically happen, and a breach only takes one weak point. Conduct security trainings, especially for admins, and get feedback on those trainings so you can improve them. Reward employees for finding weaknesses and pointing out potential vulnerabilities. Ensure employees feel engaged and cared for, since disaffected employees are less likely to care about security.
You want employees to be so motivated that they are willing to, for instance:

#2 Follow all Best Practices for General Security
You need to control who can access what, and how.

Keep your security solutions and network systems up to date, by patching promptly, enforcing strong passwords, using MFA + SSO, employing least-privilege protocols and zero-trust policy, encryption mechanisms for sensitive data both in transit and at rest, etc. Don’t forget the big picture too:
- Make funding for security a top priority, because even the best policies, procedures, and methods will fail you if they’re not fully implemented due to budget constraints. Accept that this priority must be ongoing, since risk assessment and management must be continuous and adaptive or you’ll inevitably fall behind.
- Put asset inventory programs in place for hardware and user software, and employ a central repository of all external components used by your products and tools so you can monitor and control any potential security risks they may introduce. You can’t effectively protect against vulnerabilities you don’t know exist.
- Wherever possible, centralize security policies, methods, practices, etc. The more fragmented your security landscape is, the more likely something will slip – and you might not even know it. You need company-wide visibility, security policies, and control across your infrastructure (Atlassian Access provides this).
All these general best practices apply as much to Atlassian Cloud as any tech environment. Read more about what Atlassian recommends for securing your Atlassian Cloud platform, including setting up MFA, using Atlassian Access to enforce MFA and to set up SAML SS.
#3 Do the Same for Data Exchange
It’s easy to get caught up in thinking of your organization and its network as a closed system that you can defend like a castle. But in this interdependent, interactive tech world, data has to go back and forth constantly between you and other systems.
So make sure you apply all those same security principles and approaches to inter-system communication, especially where data is exchanged with third parties, such as add-ons, plugins, integrations, vendors, et al. Each of those represents a potential hole in your defenses. The goal has to be to make it as hard for an intruder to breach your security through a third party as it would to do so directly.
And because data exchange involves another party, you need to build a good working relationship with that party, to work together to secure both sides of the exchange. Security, in this case, is a group affair.
In the case of Atlassian Marketplace apps, always study the app’s Privacy and Security tab.

Here the vendor explains the policies and procedures they have in place for data storage and management, security and compliance, and privacy, as well as listing any relevant security-related certifications.
#4 Define Where Data Belongs
Establish a clear policy on what data should and shouldn’t go into a particular system, based on what can be used to penetrate your security. We’re not talking about CUI and other generally sensitive data.

This is:
and other data that could be used to breach, to gain further access once inside, to corrupt or alter data, etc. All this must be store in secured locations, for production systems AND for dev/test systems; the latter can easily become vulnerabilities because it’s easy to think an intruder can’t do any real damage from there.
Use custom security schemes (like Issue Security in Jira, or group permissions and page-level restrictions in Confluence) to lock down access to sensitive data to only those who truly need it. Store as much authentication information as possible in central locations, to minimize the number of places you have to protect. For instance, if Confluence has pages for different dev/test systems, keep all login information for them in one page rather than storing it in each system’s page.
#5 What if Someone Gets in?
All the above practices help keep intruders out, and minimize what they can do if they get in. But you can’t stop there. Vigilance is required to identify when an intruder has gained access – an intruder who remains undetected has more time to penetrate further and do more damage.
The steps an intruder takes to achieve their goal, whether it’s ransom, sabotage, hijacking, espionage, or so on, leave traces behind. And those traces can be identified. Atlassian system admins should be monitoring for a variety of activities which, individually, an employee might do for legitimate reasons, but in a series of actions can form a suspicious pattern that’s worth investigating.
Beacon Can Help
All the monitoring described in #5 can be time-consuming – and therefore expensive, especially for a large organization. Fortunately, Atlassian is stepping up to help security teams monitor for and identify security risks.
Real-time and Reliable Visibility
Beacon – currently in public beta – builds on an internal anomaly detection program Atlassian developed for their own security teams; it won a 2022 ARN Innovation Awards in the Vendor Innovation category. They describe it as “an intelligent threat detection engine, built for Atlassian cloud products.” Beacon provides a system of intelligence over your entire Atlassian Cloud suite, ingesting user activity and alerting you to review events that might post a risk.
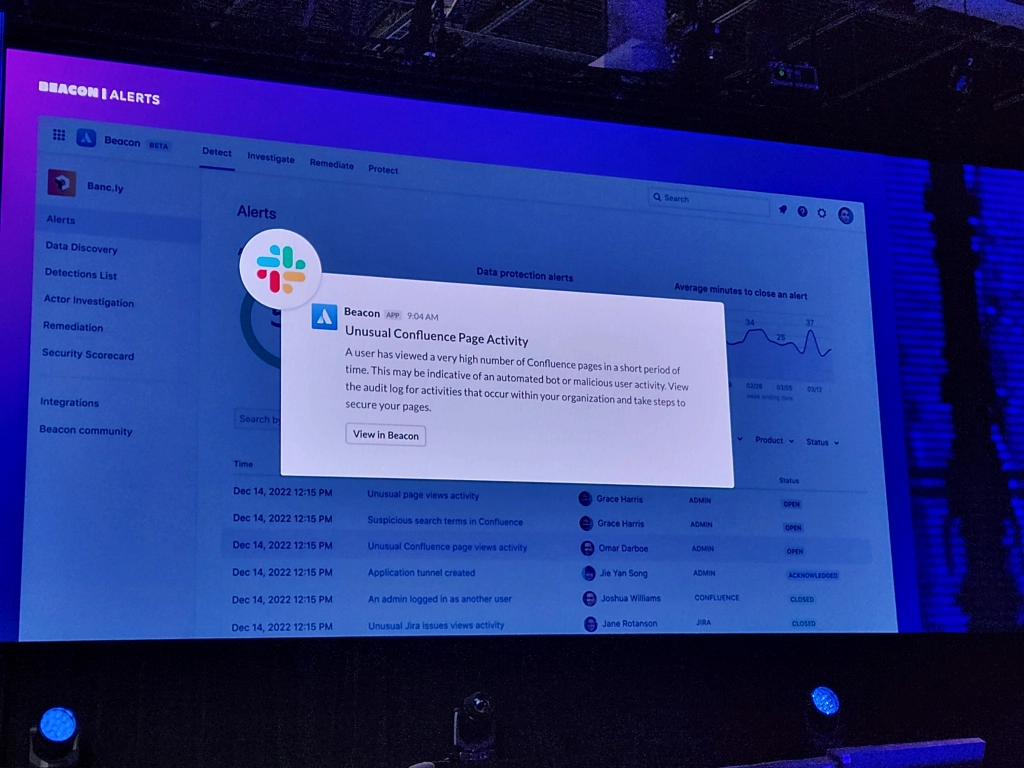
How does it work?
Beacon continuously monitors your Atlassian Cloud products for five different kinds of events:
When Beacon identifies an unusual event, it alerts you with details like user location, previously triggered alerts, and recent user activity. Atlassian also provides an ever-growing Detection Library, a catalog of detections to familiarize yourself with each alert you may receive. Some detections have instructions on testing or checking settings within the Admin hub.
Beacon also integrates with Teams, Slack, and SIEM so your teams can receive alerts where it’s most useful to them.
You can learn more about Beacon, and request to join the beta testing phase, on Atlassian’s Beacon product page.
With Beacon, you have visibility where it counts, and can act before suspicious activity becomes an incident.
Oxalis Is Here to Help
We provide Atlassian consultancy services to better enable businesses to be more productive while also enabling efficiency. As an Atlassian Platinum Partner, whatever your need, the team at Oxalis can help you scale, develop, and grow.






